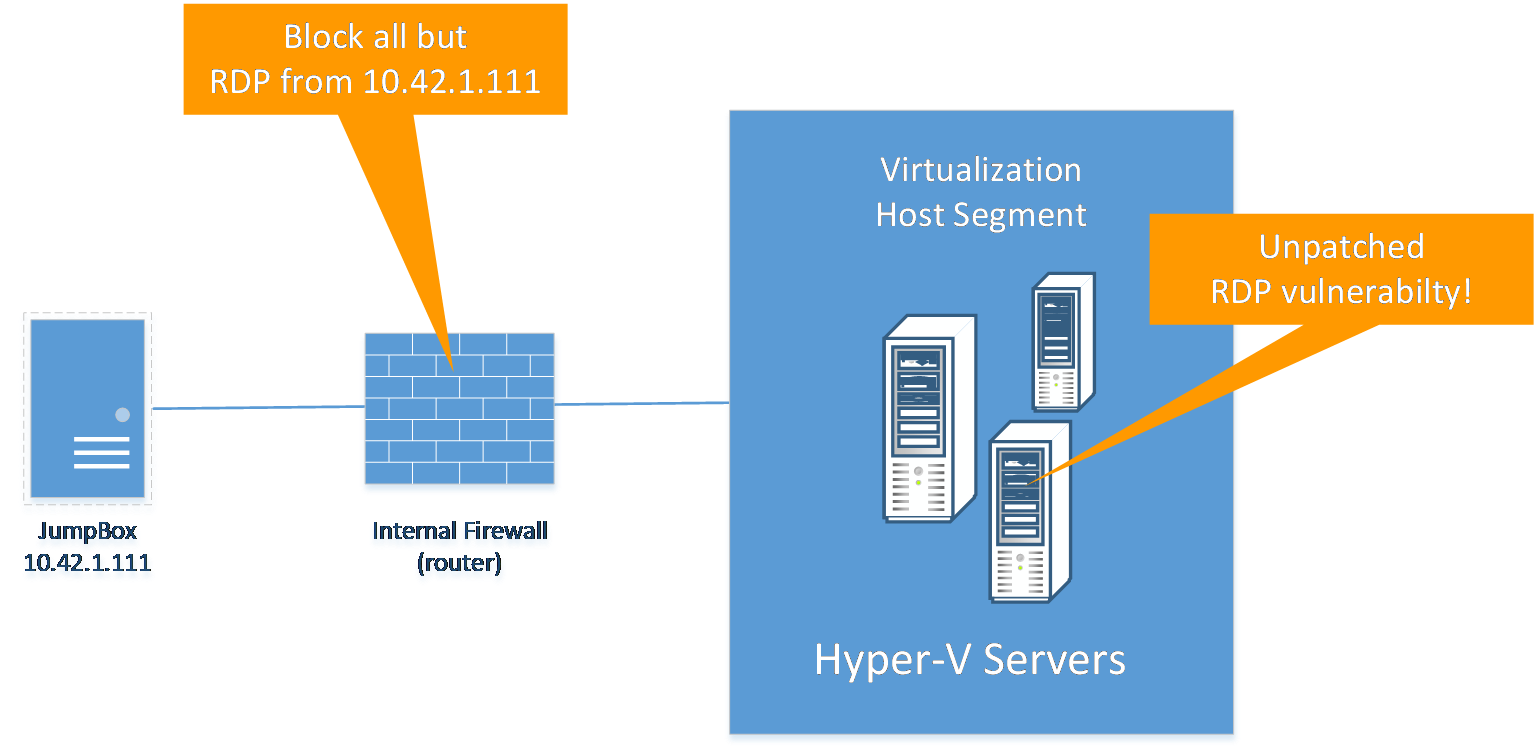
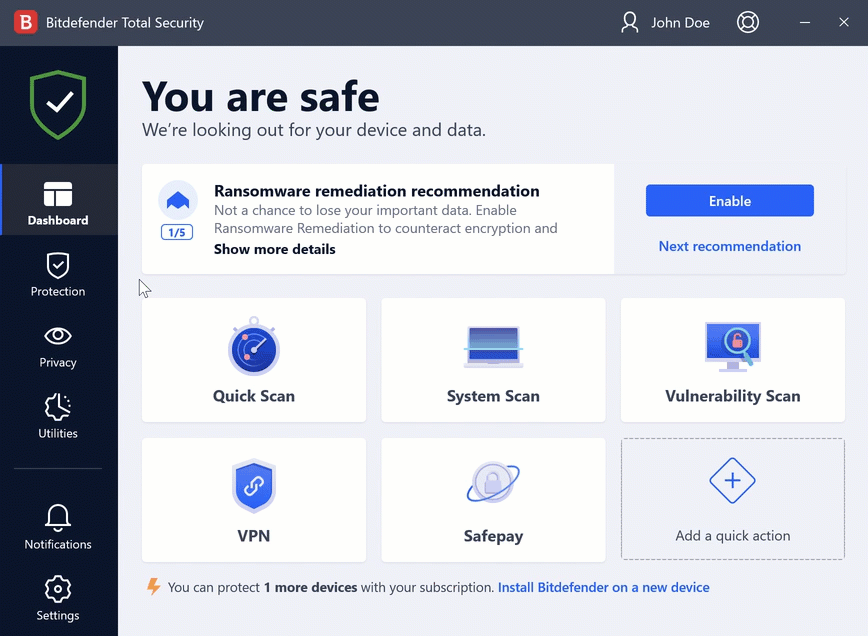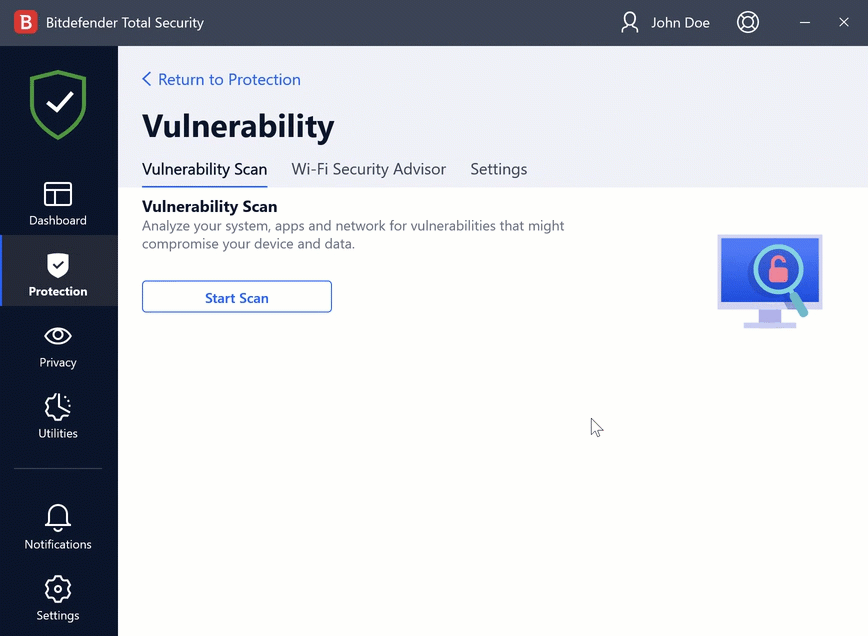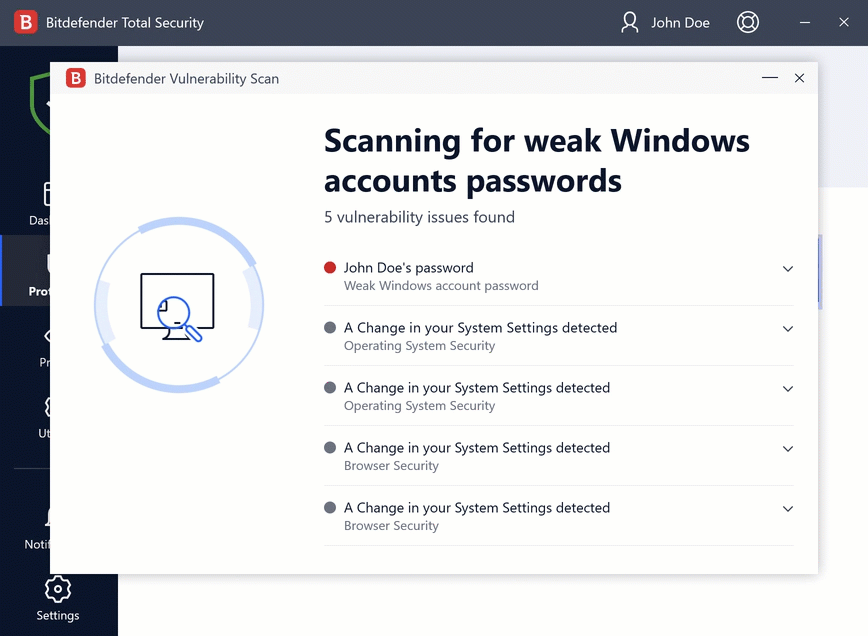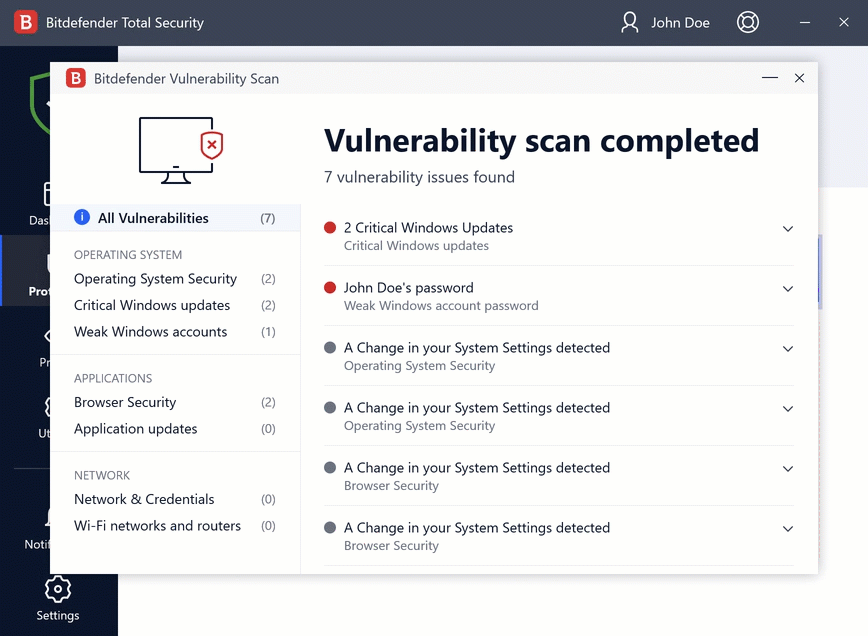
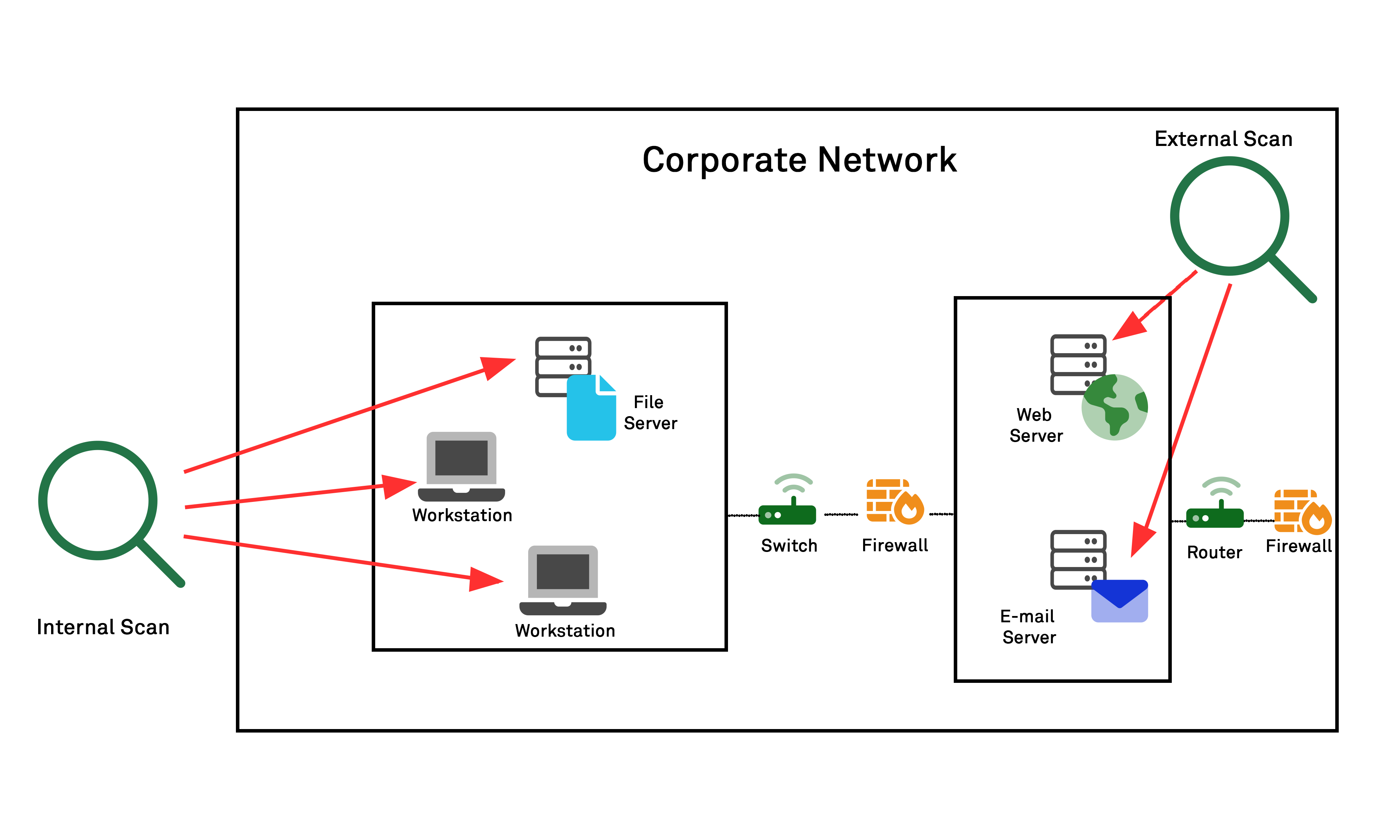
SecPoint Penetrator 1U Rack Mountable - 8 Concurrent IPs Vulnerability Scanning Appliance (1 Year) | Cybersecured - a service of Go4Smart bv
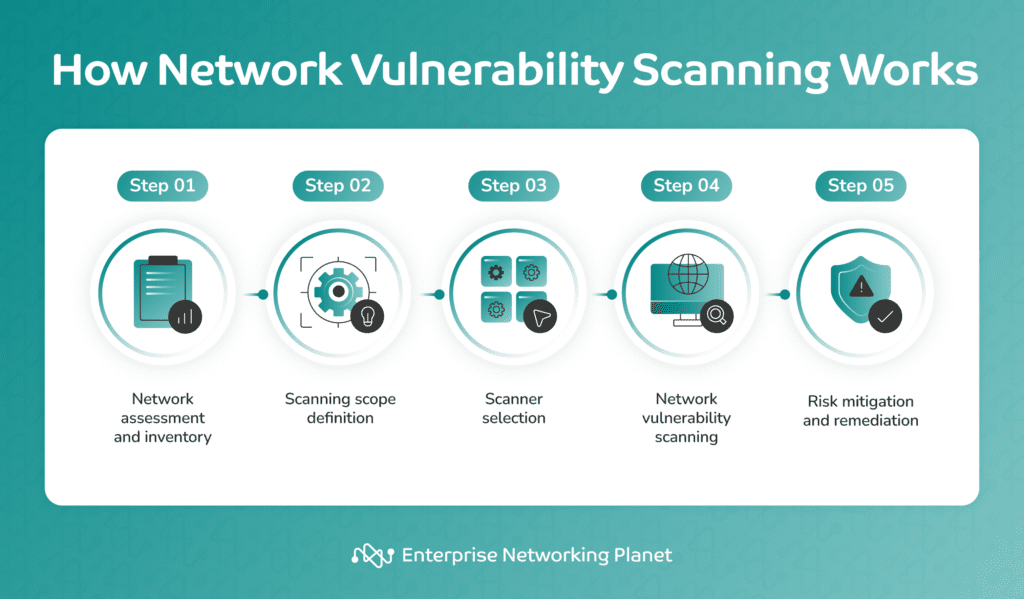
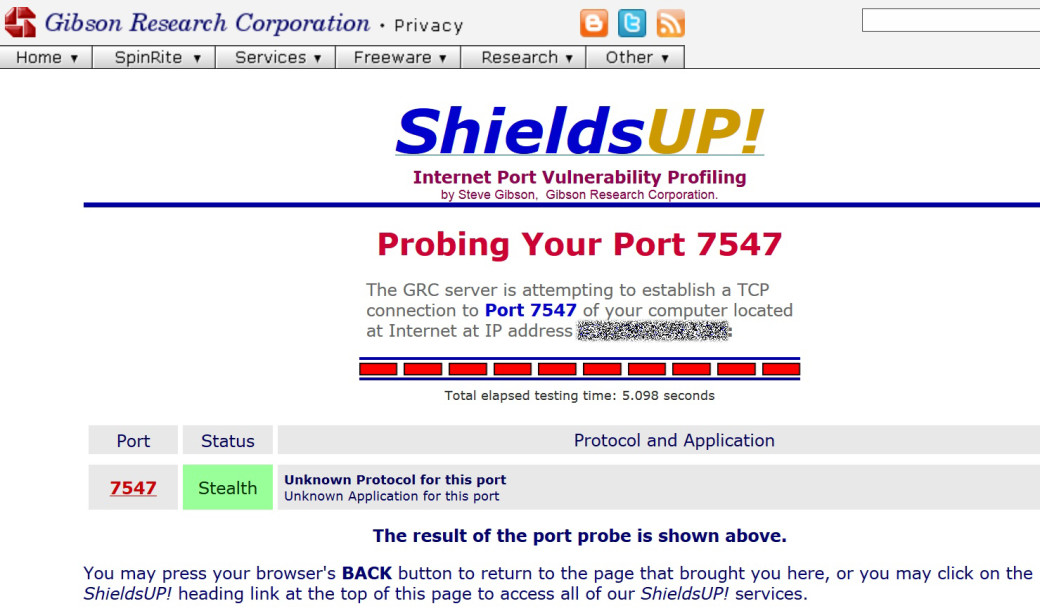
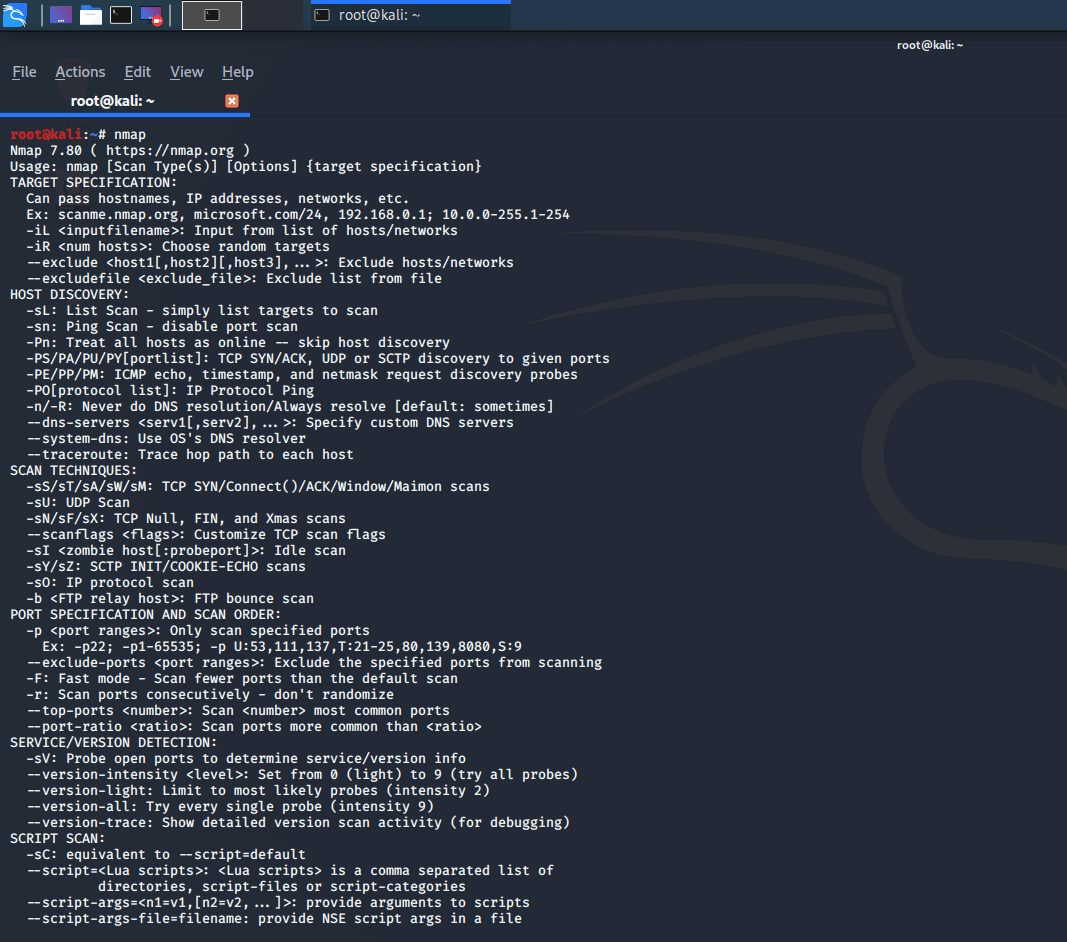
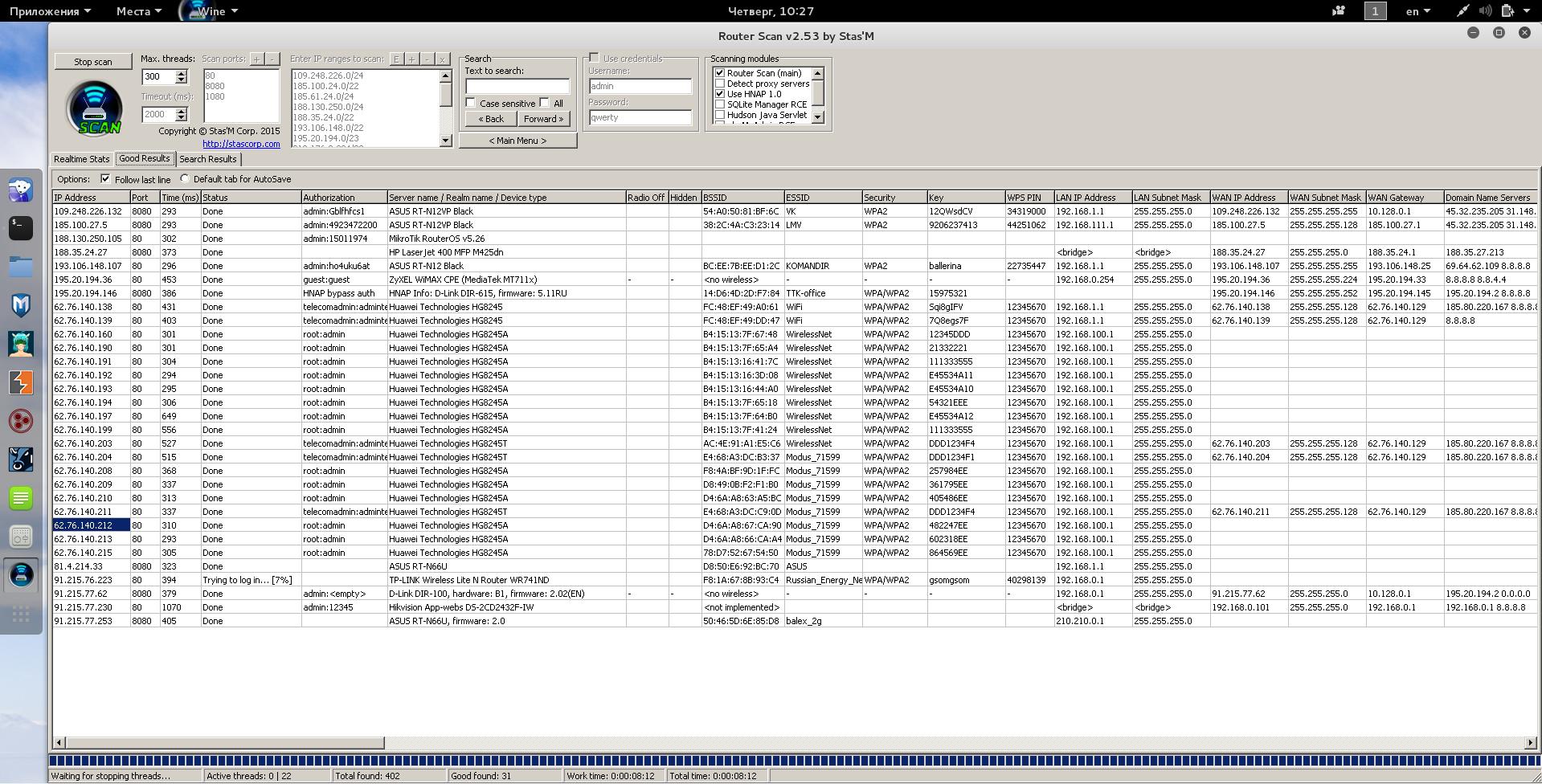
GitHub - peace27-96/Router-Vulnerability-Scan-Tool: Tool able to check the security level of a router. Check if the router is vulnerable to DNS rebinding and if there are any known CVEs or exploits.